Overview and Examples
BI row-level permissions are
based on filters and rely on target data that is modeled to work with
those filters. It is usually necessary to enhance existing data to
include information that works with the filters that you want to use.
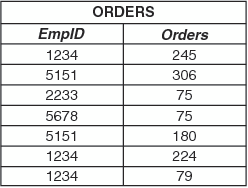
For example, consider a four-person company with a flat organizational
structure and a business requirement that each employee sees only
his or her own order information. The order information is stored
in this table:
Assume that you didn't
import users (so you don't have SAS.ExternalIdentity values in the
metadata that correspond the EmpID values in the ORDERS table). To
avoid setting up a different filter for each user, you decide to use
the SAS.PersonName identity-driven property. Create a table that maps
each user's PersonName (from the Name field
on the General tab of the user's definition)
to the user's employee ID. The following figure depicts how that table
is used to prescreen the data for each user.
Another simple example
is to subset employee performance information based on each manager's
external identity value, as depicted in the following figure.
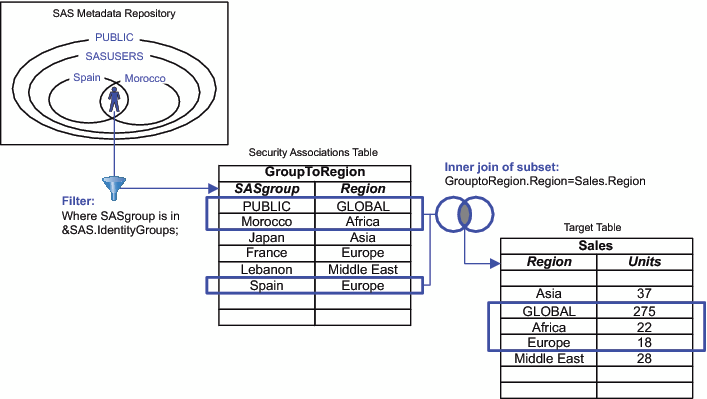
Another example is to
subset sales information by each salesperson's geographic responsibilities.
Assume that there is a metadata group for each country and that some
employees have responsibilities in multiple continents. The following
figure depicts continent-level subsetting based on each salesperson's
metadata group memberships.
This approach provides
aggregated retrieval and flattens the group structure. Each user gets
all rows that are permitted for any groups that the user belongs to.
To enable everyone to see the global totals, the security associations
table includes a row that pairs the PUBLIC group with global totals.