Variation 2: Functional Separation
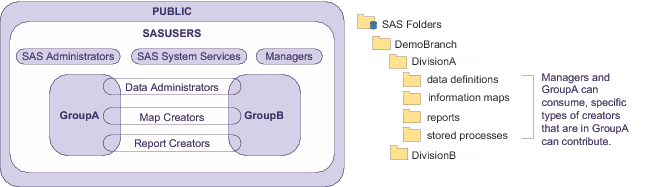
This example includes three custom
groups that represent users who have specific job responsibilities
(Data Admins, Map Creators, and Report Creators). Each division folder
has separate subfolders for different types of content (data definitions,
information maps, report definitions, and stored processes). Supplemental
Write access in each folder is limited to members of the appropriate
functional groups as follows:
Note: Access for these functional
groups is also limited by divisional affiliations. For example, only
DivisionA's report creators (and SAS Administrators) can add, update,
and delete items in DivisionA's reports folder.
Functional Separation
Here are some details
about this example:
-
On DivisionA, users who aren't in the Managers group, GroupA, or SAS Administrators are locked out. Such users can't see or traverse DivisionA or any folders in the DivisionA branch. Managers and members of GroupA have supplemental grants of ReadMetadata and Read permissions on DivisionA; these grants flow through the entire DivisionA branch.
-
On each content type folder, one or more functional groups has a supplemental grant of WriteMemberMetadata permission. However, functional group access is also constrained by division-level ReadMetadata access. For example, even though all report creators have WriteMemberMetadata permission on the DivisionA reports folder, only those report creators who are members of GroupA can see the folder.
-
You might choose to put the supplemental grants of WriteMemberMetadata permission in additional ACTs (such as MapCreators ACT, ReportCreators ACT) instead of using explicit settings on each folder. Using ACTs is more centralized, which is beneficial in accommodating later changes to the pattern. Of course, the more divisions you have, the more work it would be to update explicit settings, so the more valuable it would be to centralize settings with ACTs.
-
Consider how you would handle an exception requirement. For example, to let a particular data administrator who isn't in GroupA contribute to the DivisionA data definitions folder, you might give that user a clear path of grants of ReadMetadata permission to the folder and supplemental grants of WriteMemberMetadata and Read permissions on the folder.