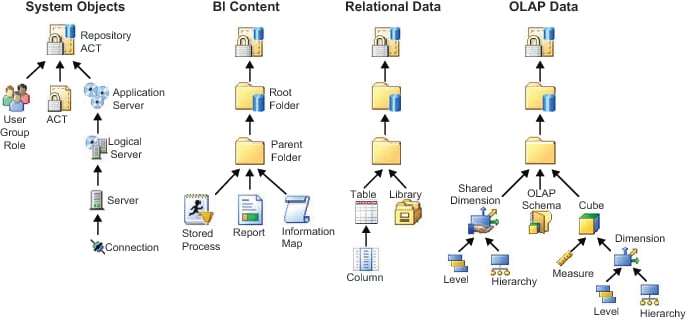
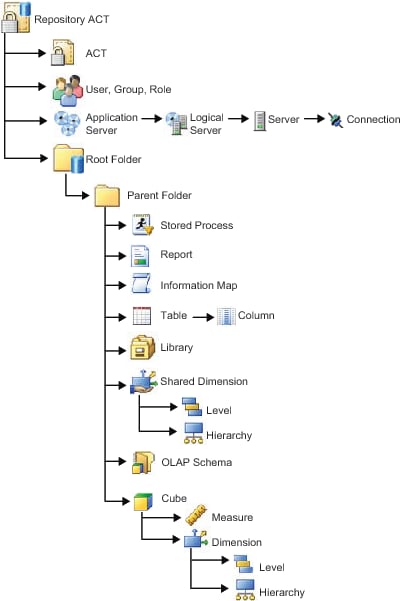
Object Inheritance
In the metadata
layer, parent objects convey their effective permissions to child
objects. Children inherit the net effect of their parents' access
controls, not the access controls themselves. The following figures
depict inheritance paths in a foundation repository. The arrows in
the first figure flow from child to parent (for example, a table inherits
effective permissions from its parent folder). The arrows in the second
figure flow from parent to child (for example, a folder conveys its
effective permissions to the items that it contains).
Here are some details
about the preceding figures:
-
Any custom repositories are represented as folders (immediate children of the foundation root folder). Although these folders inherit permissions from both the foundation root folder and the repository ACT of the custom repository, access to objects within the custom repository branch should be managed from the folder side whenever possible.